
Hello, PUBG players,
As part of our commitment to keep you posted on our anti-cheat solutions, we wanted to give you a quick update on what we've been doing the last few months. There’s a lot in the works on the anti-cheat front and while we can’t get into specifics on everything, as doing so could actually harm progress, we wanted to go over a few categories to show where we’re at and where we intend to go.
- Reinforcement of Technical Measures
- Improvement of Anti-cheat Solutions
- Unauthorized Program Detection Improvements
- Addressing Vulnerabilities in the Steam System
- Increased Legal Action
Reinforcement of Technical Measures
There have been various types of attacks made by cheat programs over PUBG’s lifetime, and while we have taken action and added multiple security measures to improve efficiency and respond to each type of attack, this will always be a never-ending battle. First, let’s go over how these cheat programs operate in general and the technical reinforcement we’ve have made based on this.
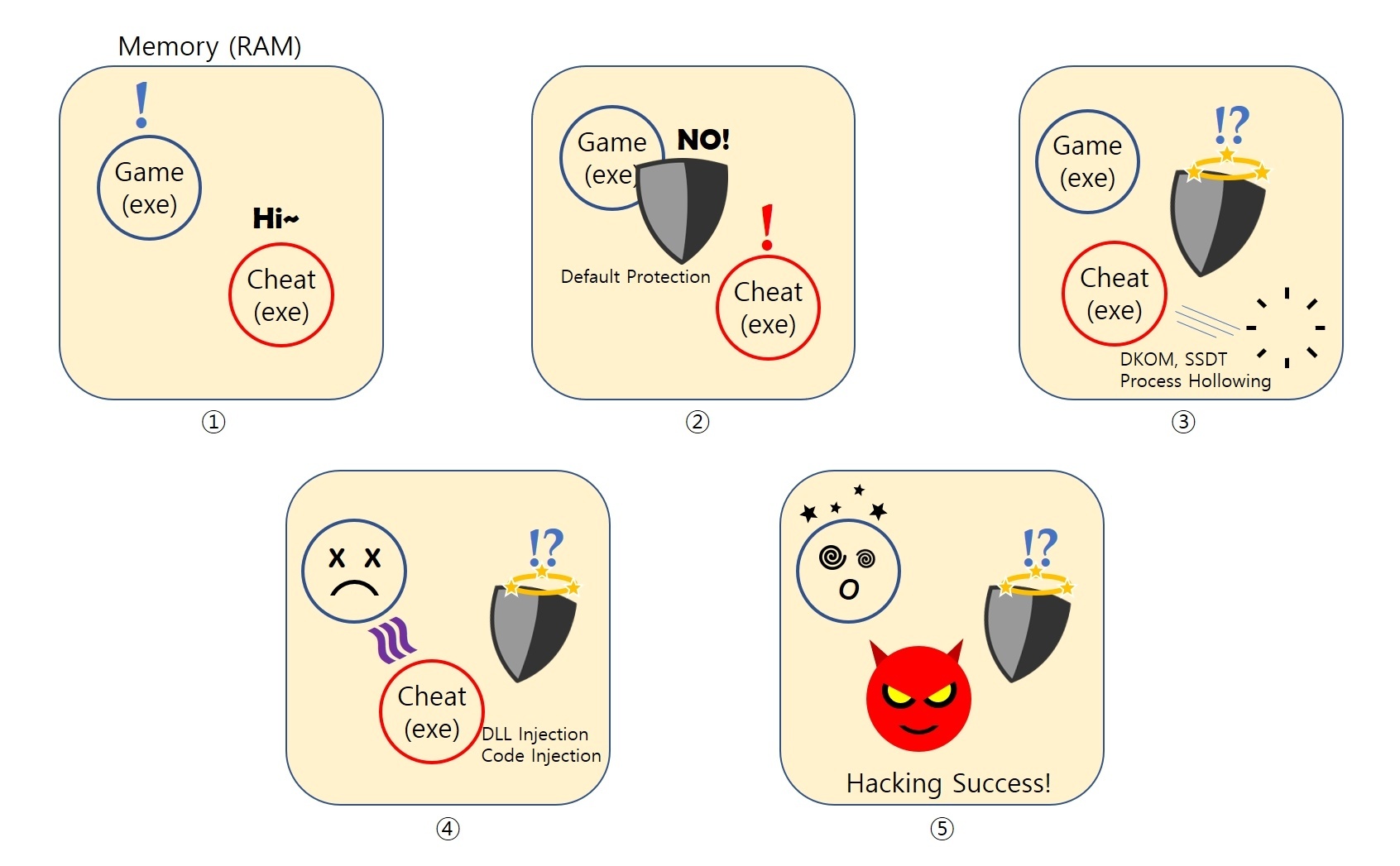
- When a cheat program (exe) and the game (exe) launch, relevant data loads onto system RAM simultaneously.
- A default protection from the game process or a 3rd party anti-cheat solution gets activated.
- This is a preliminary protection phase to block other processes from accessing this process.
- The cheat program process attempts to make the protection technology from #2 ineffective and successfully gains access to the game process memory.
- Being able to access memory means being able to change game related info.
- The most notorious cheats used for this are DKOM, Process Hollowing and SSDT hooking.
- Being able to access memory means being able to change game related info.
- The cheat program with game process memory access can collect various data and modify or copy it to provide illegal features that are not provided in the game. The most representative technique used here are DLL injection and Code injection.
- DLL injection: Injects the DLL file to a certain process. Uses LoadLibrary() API from Windows.
- Code injection: Injects execution in the target process. Uses CreateRemoteThread() from Windows.
- DLL injection: Injects the DLL file to a certain process. Uses LoadLibrary() API from Windows.
- Memory space obtained can be read freely or falsified/modified to provide features that are not actually provided in-game.
DLL injection is the oldest and most widely used hack method. DLL injection places a certain DLL file into the game process forcefully. When this attack is done successfully, this DLL code will be trusted as if it is the original game code. Consequently, the game process can be modified as the hacker wants by using this DLL for hooking into and hijacking data.
Blocking DLL injection attacks has been a high priority for the anti-cheat team. In the early development phase of PUBG, there were also compatibility issues where programs such as Steam and Discord were incorrectly recognized as attempting to inject DLLs or had DLLs recognized as malicious code.
Kernel driver attacks are another type of hack we’ve experienced. Kernel driver is a file needed for communication between hardware and comes up with a process that operates under a certain authority. As the kernel driver can bypass most anti-cheat solutions and is executed with an authority higher than the general user authority, it is much more difficult to detect.
In addition, despite Windows OS blocking unauthorized kernel driver internally, there are many cases where unauthorized kernel drivers are sold as if they are legal by exploiting security breaches and illegally traded certificates.
We could defend against this type of attack using the same method used to block DLL injections, but it would not be very effective because new vulnerabilities in the Windows OS are constantly being found, and most anti-cheat solutions employ methods similar to those used by malignant code, meaning it is difficult to tell them apart. The anti-cheat team therefore is currently protecting the memory area, which can be abused by hackers, with the highest priority using encryption to effectively respond to attacks using kernel drivers, and is doing its best to apply this method to a wider scope of areas.
We are also strengthening various technical responses by encrypting the communication protocol between the client and server or re-verifying the result value in the client, for example, so we can stay ahead in our fight against hack programs.
Improvement of Anti-cheat Solutions
In addition to the technical protection explained above, PUBG also utilizes external anti-cheat solutions to protect the game process area. As previously announced via press releases, etc., we currently use two anti-cheat solutions: BattlEye and Uncheater. They protect the game process area and detect various attempts used to circumvent the anti-cheat solution at the same time.
On top of these protective anti-cheat solutions, we have also applied a machine learning technique that analyzes our players' usage patterns and have built a system that can detect abnormal game patterns or actions that interrupt the normal operations of the game coming from hack users. In the process of building these systems, we collaborated with numerous experienced anti-cheat solution companies and top-tier engineers, which has helped us strengthen our game's security.
We will continue to work with more anti-cheat solution companies to study new attack techniques and develop technology that can protect against these attacks.
Unauthorized Program Detection Improvements
Even with the various protections we’ve set in place, it is virtually impossible to block all unauthorized programs. For hack programs that try to go around our solutions, we are currently trying to detect whether such programs are used in-game and have them blocked right away.
The anti-cheat team analyzes around 3TB of game logs, 60 or so types of cheat logs, and over 10 million reports on average on a daily basis. Out of this sea of data, we pick out users who show abnormal patterns and after a verification process, such accounts are banned. Also, we periodically update patterns of unauthorized programs to ensure programs we’ve blocked before haven’t been modified to work again.
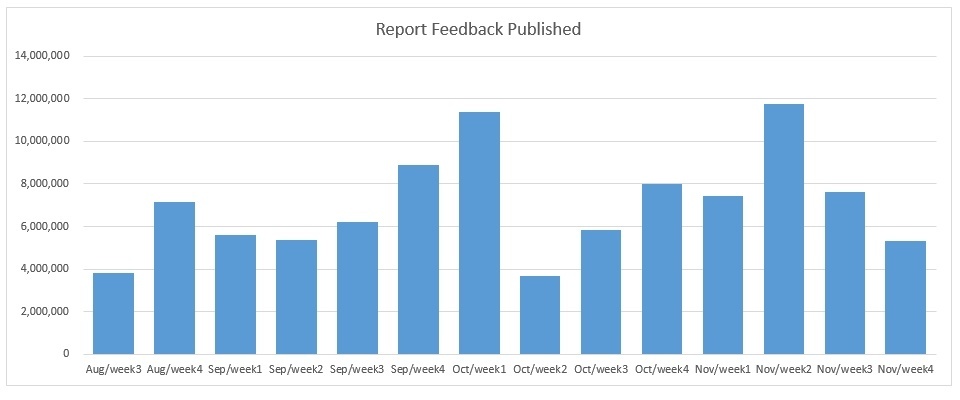
At the same time as all of this, we’re trying to improve our methods of sharing relative updates to our users. One example is the report feedback system which was introduced in the August 23rd update. Since this was implemented, over 100 million reports have been sent to users. 83% of users that received multiple reports in a single session were permanently banned, so if anyone ever thinks their report doesn’t matter, your reports are going a long way towards a fair battleground.
Below shows the weekly report feedback data from August 23rd to November 30th.
On the topic of hardware bans, we began these back on November 19th. This is a very sensitive method of banning, so we take extra precautions to ensure that PC cafes or public PCs are not impacted unfairly. We are very carefully picking out which machines are to be banned in order to prevent innocent PCs from being hit. When a hardware ban is performed, the message shown in the screenshot below will pop up and that piece of hardware will not be able to play PUBG anymore. Alongside hardware bans, we also started to ban macro mice. The plan is to expand this effort to all devices to prevent the unfair advantage of using macro devices.
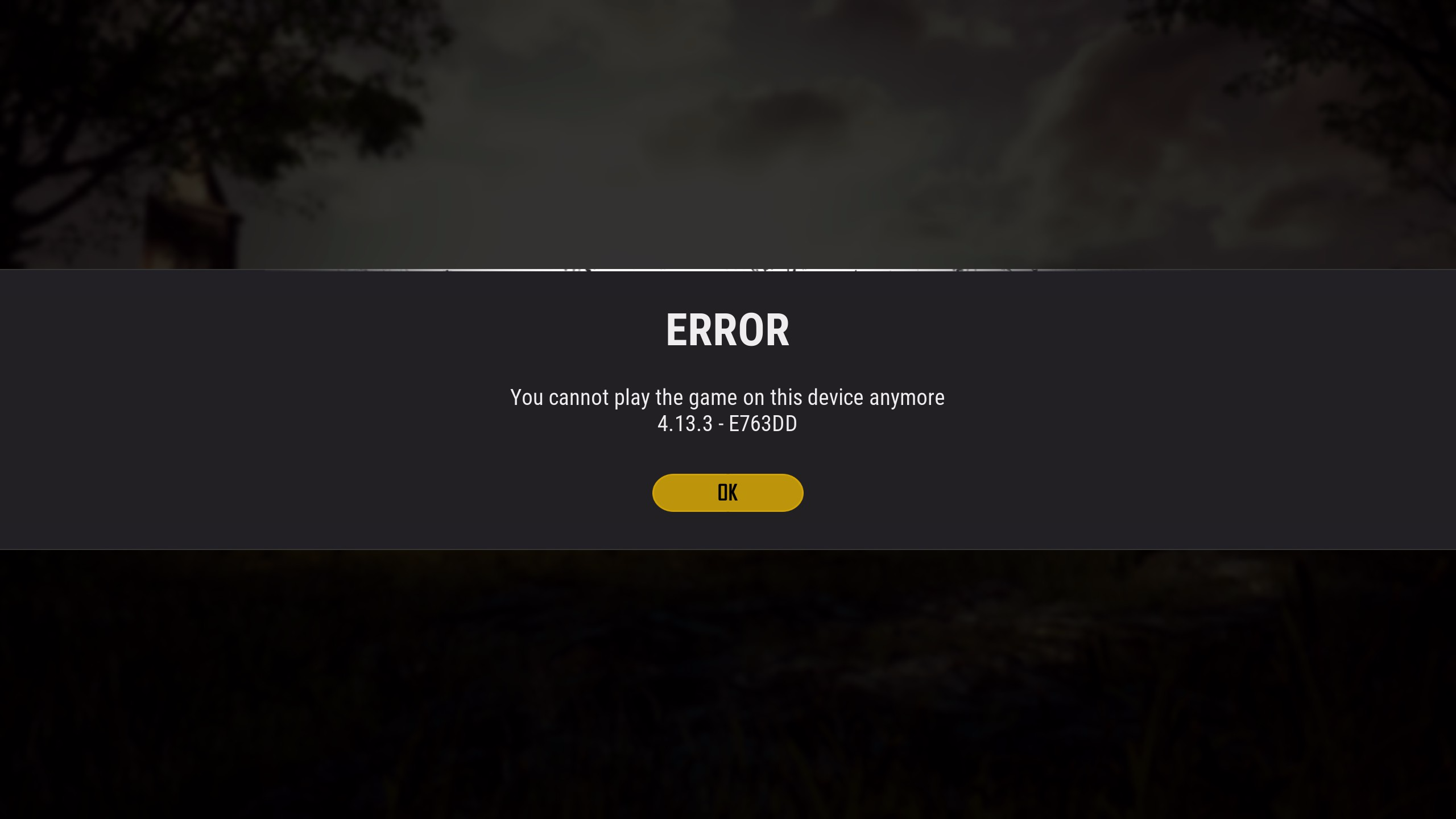
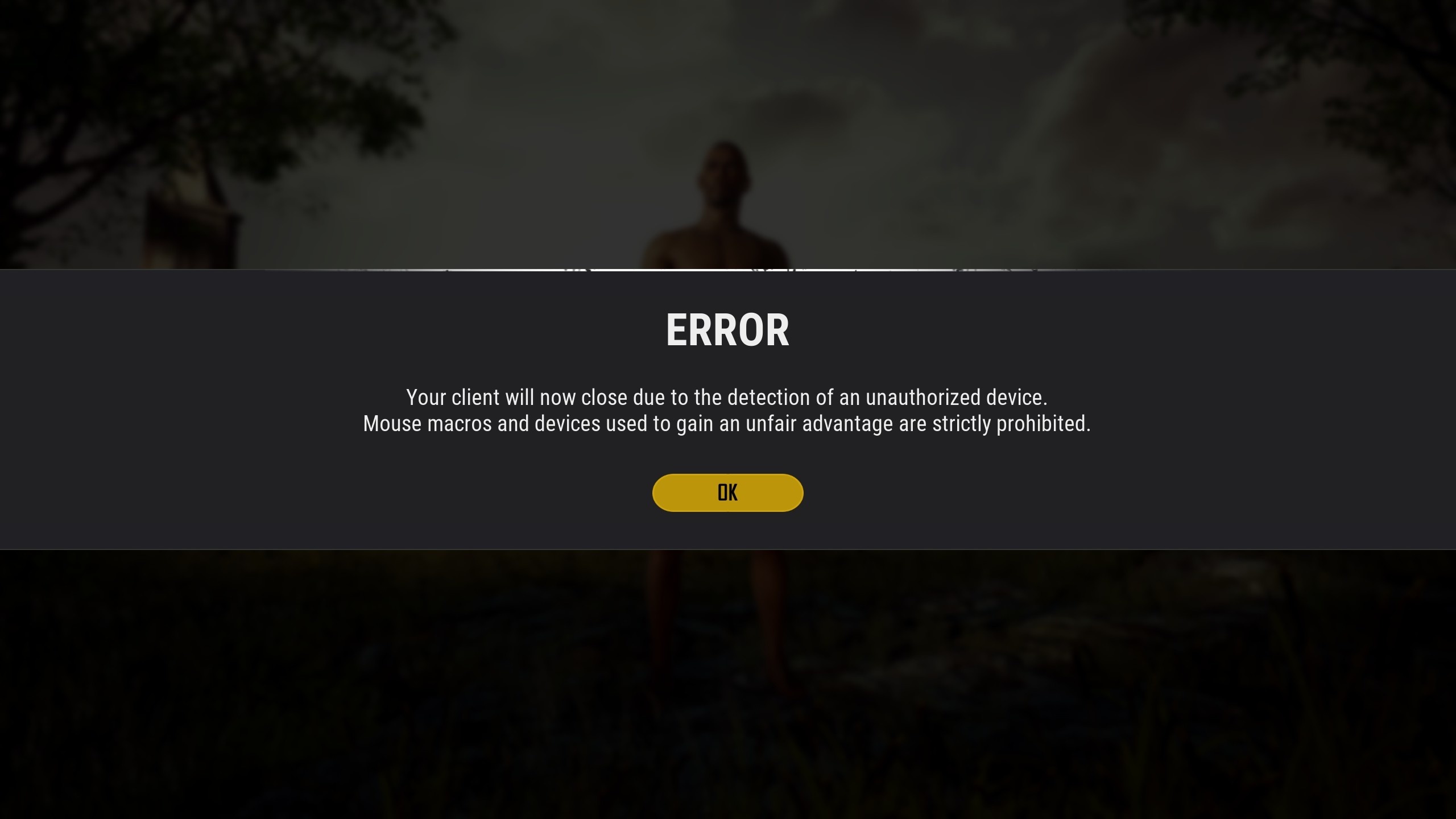
<Hardware ban message(above) / Macro mouse ban message(below)>
We currently have over 100 people monitoring the places that sell these hacks (websites, messengers, discord etc.) all over the world 24/7. Various communities that exchange information on hack programs are also being monitored closely so any elements that threaten PUBG's security can be detected and dealt with as quickly as possible.
The end goal is to ramp up preemptive action so these hackers are no longer active within the game.
We also recently added a system message that sends real-time alerts to players in a game if someone from the same session is banned. Whenever an abnormal gameplay pattern is detected in real-time or a user is proven to be a hacker mid game, that account will be banned as the game is still going on and announced to all other players in the kill feed.
Addressing Vulnerabilities in the Steam System
In addition to the methods applied within the game, we have also helped improve vulnerabilities in external platforms. As you know, PUBG uses the Steam platform. There were instances where some weak spots in the platform were exploited for illicit gain, and we improved on this with Steam and addressed the vulnerabilities so that hack program users would be punished as per normal procedure. Below are some examples of actual instances.
- Using a weak point in the Steam Family Sharing system to circumvent Steam and PUBG's restrictions
- If an account that purchased PUBG used Family Sharing to share the game with an account that didn't purchase PUBG, the account that the game was shared with can no longer play the game.
- Tampering with the game's playtime on Steam to meet Steam's minimum refund requirements and refunding the game despite having played it for a long period of time, thus playing the game free of charge
- We worked with Valve (Steam) to reinforce their PUBG playtime calculation method and Steam user software refund requirements to stop this from happening again.
- Using an account that was banned on the Live Server to access the Test Server and use hacks, abusing the fact that the Beta and Test Servers are considered to be in separate environments due to the way the Steam platform is structured
- We have changed the system so ban records are now checked across all servers. Ban records are now shared among the Live Server, Test Server, and other servers so that a player banned on one server cannot use the other servers as well.
Increased Legal Action
Hack programs that hinder a fair game environment are important to block, but those who develop, promote, and sell hack programs should always be a primary target as well. To prevent the spread of hack programs, we are working with law enforcement authorities and overseas offices to take strong legal actions both at home and abroad. Below is the outcome of the legal actions taken in 2018, and for the CN region, it is a result of close cooperation with Tencent.
- Arrested 41 in Lianyungang, China in January, 2018
- Arrested 3 in Huai'an, China in February, 2018
- Arrested 11 in Xiangyang, China in February, 2018
- Arrested 141 in Nanjing, China in April, 2018
- Arrested 1 in Huai'an, China in April, 2018
- Arrested 6 by Daejeon Metropolitan Police Agency, Korea in August, 2018
- Arrested 1 in Wenzhou, China in September, 2018
- Arrested 3 in Tangshan, China in October, 2018
- Arrested 34 in Wenzhou, China in October, 2018
- Arrested 11 by Yangcheon Police Station, Korea in October, 2018
In addition to the outcomes mentioned above, we are currently investigating hack programs sales with The Korean National Police Agency, law firms, and copyright protection agencies along with tracking the hack developers themselves. We will keep you updated as new investigation results become available.
In Closing
Each game of PUBG sees up to 100 users trying to beat already incredible odds. We understand that even one person playing unfairly can severely impact the fun of so many people, and thus we need to maintain a much higher level of security than other games.
We will continue to devote ourselves to this task and while what we have shared today are still early steps in this battle, we will not stop researching and developing new anti-cheat technologies to eliminate as many hack programs, and their developers, as possible.
We appreciate the patience and trust of all of you and will do all we can to repay that trust. Thank you for your continued support and reporting.
--The PUBG Anti-Cheat Team
